IdentityServer4 - accessing API
In the previous post, I wrote about how to get tokens from IdentityServer using a javascript client. In this post, I am going to write about how to use this token to get access to protected resources from a sample API.
As in the previous post, to achieve my goal, I used samples provided on the
github repository.
In this repo folder
I found a sample API which I copied into my local repository. After this, I executed dnu restore inside the SampleApi directory.
The SampleApi works on a different port than expected (I expected it to work on 3860, but by default it was 5000) so I changed web command in the project.json file in the SampleApi to:
"web": "Microsoft.AspNet.Server.Kestrel --server.urls=http://localhost:3860"
I could find this port in the index.html file of the JsOidc project. In this file, there is a handler for event click for the button Call Service. In this handler, the request is sent to the address http://localhost:3860/identity and this is the address on which my Api should work.
Then I was ready to run my application. I executed dnx web in three different directories simultaneously: IdSvrHost, JsOidc and SampleApi and after this I navigated to http://localhost:7017/ and I clicked Login With Profile and Access Token and I saw this screen:
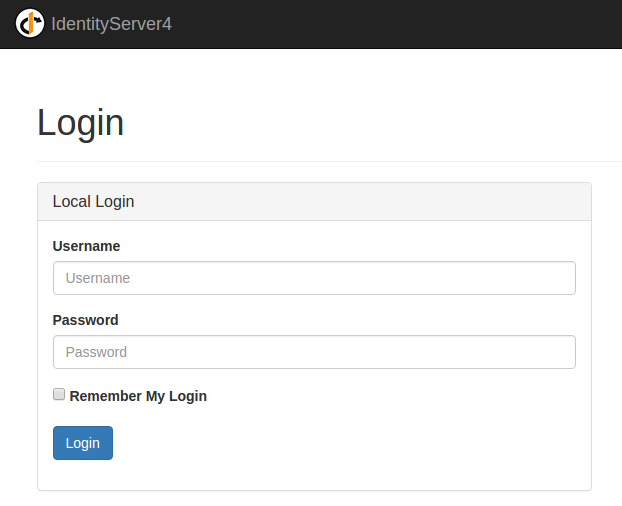
I entered the user name alice and the password alice and the I saw this:
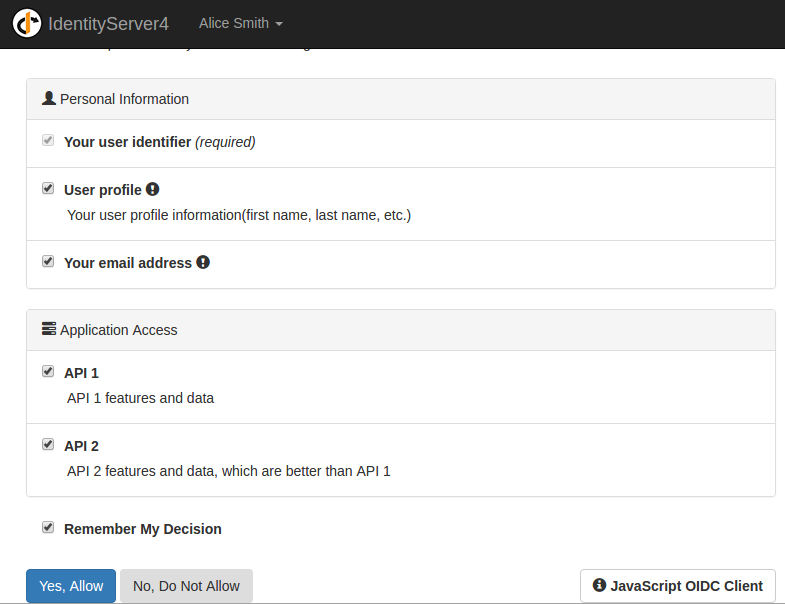
I clicked Yes, Allow and I was brought back to my JsOidc. The next thing which I did was to click on “Call Service”. After doing this, I saw a response in the pane Ajax Result, which looked like this:

This response contains users claims and this is how it was prepared:
return Json(User.Claims.Select(c => new { c.Type, c.Value }));
I was really amazed by how smoothly I went through usage examples of IdentityServer4 on Linux. After my previous experiences, I was rather sceptical if this example could even run without errors on Ubuntu but they executed perfectly. By doing this example, I checked if I can use IdentityProvider4 as an identity provider for my application but as you may remember from my previous posts, I wanted to have Google as an Identity Provider. In a future post, I’ll examine if it is possible to combine Google authentication with IdentityProvider4.
Related posts:
- Enrolling in "Daj się poznać"
- "Daj się poznać" - Project details"
- I'm holding a Project Rider EAP
- Installing ASP .NET Core 1 on Ubuntu 14.04
- My first ASP NET Core 1.0 web application
- Project setup - server-side
- Project setup - client-side
- Adding styling to my application
- Angular 2 Confirm Dialog Component
- Before going into production
- Publishing to Azure
- Setting up the Web client for Google Identity Platform
- oidc-token-manager library with Google Identity Platform - Part 1
- oidc-token-manager library with Google Identity Platform - Part 2
- Accessing API with token from Google Identity Provider
- How portable is ASP .NET Core 1.0?
- When dotPeek can save your live
- Reading code as if it were a book
- ASP .NET Core Configuration
- Getting started with IdentityServer4
- IdentityServer4 - accessing API
- Dealing with secrets in ASP .NET Core
- Google Identity Provider with IdentityServer4
- Upgrading to Angular2 RC1
- Experimenting with Angular2 CLI
- Migrating to ASP .NET Core RC2
- Epilogue: Daj się poznać series

Comments
comments powered by Disqus